Have you heard of online banking thefts employing a program called “keyloggers” and are curious to know how to check for keyloggers and clean your system? Or have you ever wondered how passwords, user names and other sensitive login credentials are stolen from seemingly secure websites? Do you know how different keyboards are able to learn your writing style and predict words you might use next? All these tasks are often accomplished by recording the keys struck on your keyboard, a method known as keylogging. Confused? Don’t be.
This article will cover in detail what keyloggers are, how they work, and how to check for keyloggers in your system and remove them. By the end of the article, you can expect to have a fair idea about keyloggers and some precautionary measures you can take to protect your sensitive credentials.
Table of Contents
How to Check for Keyloggers and Remove it from the Computer
What is a Keylogger? What are its Functionalities?
Keylogger, or ‘keystroke logging’ is the act of logging or recording the keys pressed on the keyboard, by software or hardware means, often with the monitored individual being unaware that his/her keystrokes are being recorded. The logging program can later retrieve the recorded data from its storage area.
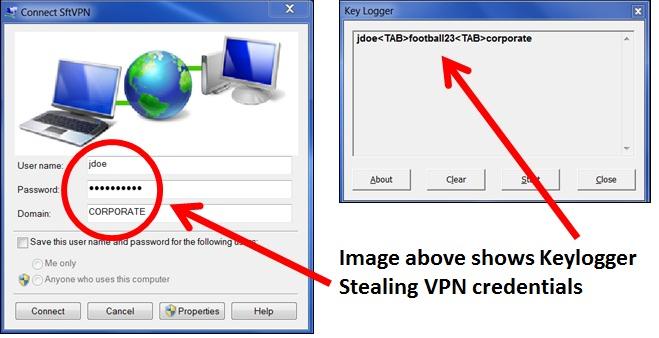
Often, keylogging is done with malign intentions to intercept sensitive and private information like credit card details, bank account credentials, usernames, passwords, and other private data. A lot of high profile bank thefts have seen the usage of keyloggers. Nordea bank had lost about 1.1 million dollars to online fraud in 2007, where the attackers used keyloggers built into a Trojan to steal credentials from users. There are many other examples of banking crimes where keyloggers have been used, mostly because they are extremely reliable to track electronic information.
Keyloggers also have a variety of legitimate applications. They are used to recognize keyboard shortcuts or ‘hot keys’. They are authorized research instruments to study writing processes and can be employed to track writing development in children. Parents can monitor their children’s internet usage with keyloggers, and employers can track the usage of their workstations for non-work purposes. Law enforcement agencies utilize keyloggers for surveillance purposes to analyze and track usage of personal computers in crimes.
Are Keyloggers Legal?
At this point, you are acquainted with the capabilities and the wide range of applications where keyloggers can be exploited. You must be wondering if the usage of keyloggers is legal. The answer to this question is both yes and no. There has been much debate about this topic, and the arguments both for and against are perfectly valid.
The biggest argument against keyloggers being used is that their usage invades privacy at a large scale. Every individual is entitled to protect their privacy, and there is a very fine line between invading one’s privacy and authorized surveillance. The very fact that even governments can’t draw a line on privacy infringement, makes drawing up concrete laws even more difficult. Hence, usage of keyloggers is still legal. Attempts are being made to interpret protective laws in such a way, that monitoring the general public’s keystrokes is deemed unconstitutional. If keyloggers are used for criminal purposes, they are obviously illegal and the criminals can be implicated in a court of law.
Types of Keyloggers
Keyloggers can be both, software and hardware based. The software-based ones are computer programs which work with the target computer’s software. There are several types which employ different methods to capture the keys being hit by the user.
- Some keyloggers are designed to grab and record entries in web-based forms. As soon as the submit button is pressed, the keyloggers capture the data before the values are passed on to the Internet.
- Another category of keyloggers hides in the operating system by gaining root access. Programs that gain root access reside at kernel-level, the kernel being the central module of the operating system. These keyloggers are difficult to detect and remove because user level applications do not have permissions to modify kernel level programs.
- Javascript based keyloggers inject a script tag with malicious code into the web page and listen for keyboard events and record the inputs.
The hardware keyloggers do not depend on any software installed and exist at the hardware level of the computer. These hardware keyloggers can be added physically to the keyboard in the form of a hardware circuit. They can also be implemented as BIOS level firmware (BIOS is the low-level hardware which initializes the hardware when the computer is powered on). There are hardware devices that are able to sniff packets being transmitted from wireless keyboards and mouses to their respective receivers.

How to Check for Keyloggers and Remove them from the Computer
Since keyloggers have legitimate usages as well as illegal ones, you must be wondering how checking for keyloggers can be done and how to remove them. Some keyloggers are very sophisticated and use very complex methods to hide as legitimate processes running in the background. It is often next to impossible to scan for these keyloggers. The simpler keyloggers can be detected and removed. Here are some ways to check for keyloggers and remove them.
1. Analyze Winlogon.exe Process using Task Manager
The Winlogon.exe is a critical component of the Windows operating system. It is a process that handles the loading of the user’s profile when logging in. It also handles the secure attention sequence. This is the CTRL+ALT+DELETE key combination that had to be pressed in older versions of Windows before signing in. This ensures that you are signing in to a secure desktop and no other program is impersonating a sign-in dialog or monitoring the password you are typing. Windows Vista and newer versions have significantly changed the roles of this process (CTRL+SHIFT+ESC).
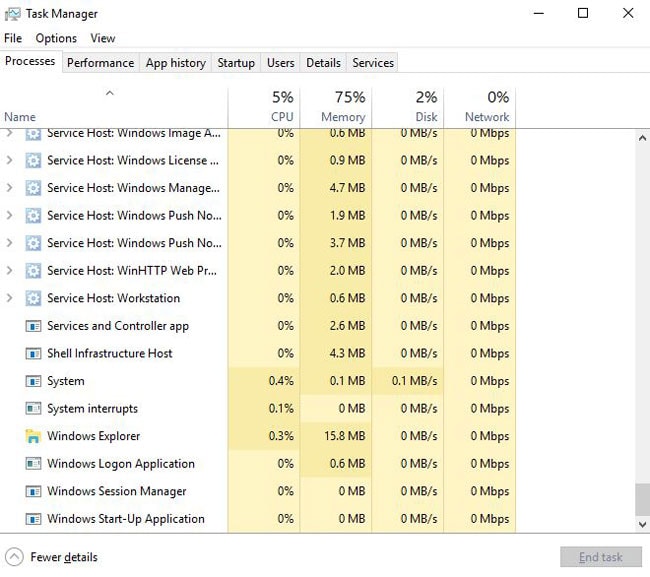
This process is often targeted during security attacks which modify its function and increase its memory usage, which serves as an indication that the process is compromised. Also if two or more duplicate Winlogon.exe processes exist, one of the processes might be a keylogger function and the task manager can be used to end the process. You can do this by pressing CTRL+SHIFT+ESC key combination (On Windows 7,8 and 10) to bring up the task manager. Select the Processes tab. If you find two or more instances of the Winlogon.exe process, click on the process with the duplicate number to select it and press End Process to end it.
2. Installed Programs
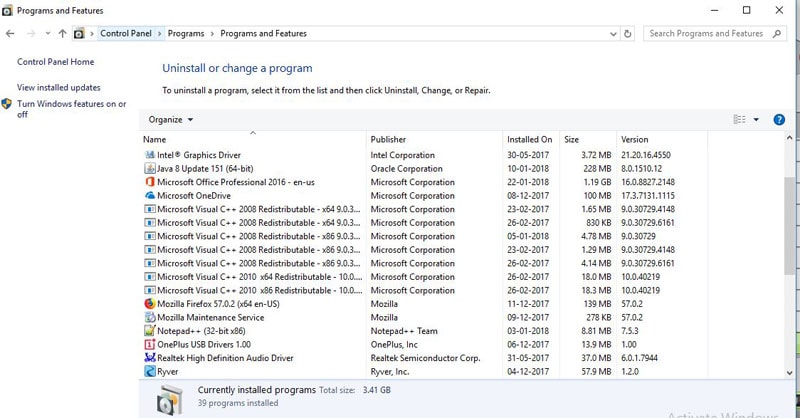
If the attacker is careless and does not keep the keylogger hidden, it can be discovered in the installed programs list. You can click on Start and go to Control Panel. Select Programs and Features or Uninstall a Program. You will be presented with a list of programs and software installed on your machine. Check the list for any programs you have not installed. If you find any suck program, right click on it and select Uninstall.
3. Anti-Keyloggers
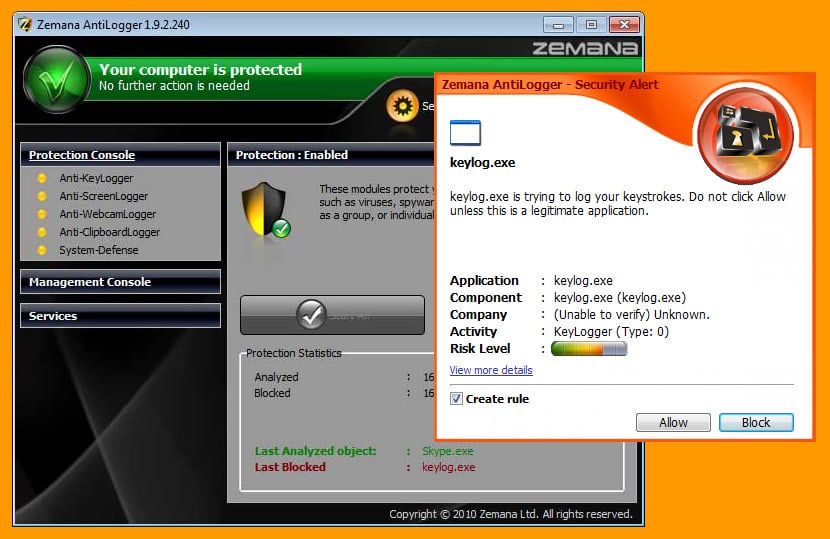
These are software designed to scan for keyloggers in your system. They tend to be more effective than generic anti-virus programs because they are designed specifically to detect keyloggers. They usually compare all files in your computer against a database of keyloggers. Any similar behaviors discovered by comparing might point out a potential keylogger. If the keylogger is very sophisticated, anti-keyloggers might fail to detect them. Anti-keyloggers will be used frequently in public computers in the interest of the safety of the users. These computers are more susceptible to such software and hence, must often run the anti-keylogger program regularly to ensure that they are not infected and safe for public use. Users themselves should also resort to safety measures to protect their data and privacy.
4. Anti-spyware and Anti-virus Programs
Many of these programs have begun adding known keyloggers to their databases, and you must make sure that your databases are always updated to include the latest additions. These programs might be able to check for keyloggers that are software-based and cleanse, disable or quarantine them. The detection might be difficult if the malicious program or virus with the keylogger is very sophisticated and hides as a legitimate software. Also, anti-virus programs with lesser permissions and privileges will not be able to detect a keylogger with higher privileges. For eg., a spyware program with user-level privileges only cannot detect a kernel-level based keylogger. Many anti-virus programs categorize keyloggers as potentially malicious or potentially undesirable. You must hence make sure the program is detecting such software by default. Else, you might require configuring the anti-virus program accordingly.
Useful Tips to Protect yourself from Keyloggers
At present, you know how to check for keyloggers and remove them from your computer. This should protect you from certain groups of keyloggers. Here are some more precautionary methods you can use to protect yourself from keyloggers. Keyloggers vary widely in the way they work and try to intercept data. Hence the methods you employ to protect yourself should target the way the keylogger works. Hence, some methods might work very well with a certain group of keyloggers, but might be completely useless against others. Also, the authors of keyloggers can update their keyloggers to adapt to the countermeasures taken by you. Keyloggers chiefly attempt to collect your confidential data, so the following are the most common ways to protect yourself:
1. Use One-time Passwords or Two-step Authorization
One time passwords can be a very effective solution, as the passwords become invalid as soon as they are used. So even if a keylogger is installed on your system, the intercepted password becomes useless after one session. This effectively protects your private data.
Two-step authentication is also a very good measure to prevent yourself from keyloggers. A two-step authentication process involves the user entering his/her credentials first. After entering the credentials, they receive a code or password on a registered mobile number or email id. The user is then required to enter this code to get validated, thus adding the extra layer of protection.
Since the generated code or password gets invalidated after one use, this also protects your sensitive data in a similar way one-time passwords do. This method will be ineffective if the attacker has remote control of your computer and makes invalid transactions as soon as you are established to be a valid user.
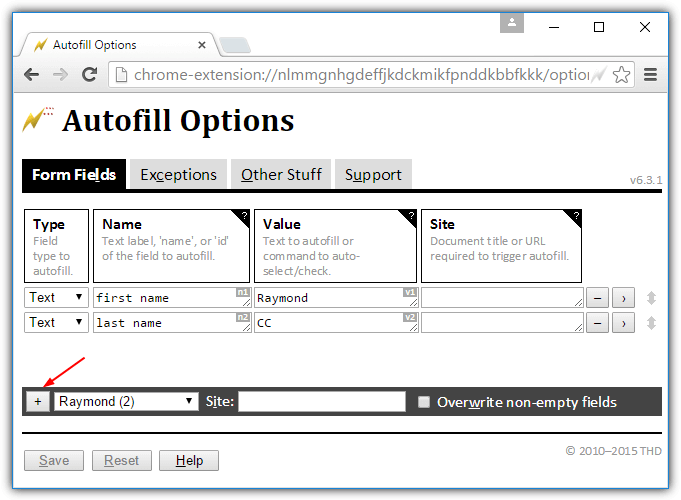
2. Automatic Form Filler Programs
You can use programs which fill in your data automatically without requiring you to type in the data. The keylogger is unable to detect any data since you don’t have to manually type it in. However, anyone with physical access to the device can install software to record this data from elsewhere. The data can be recorded from the operating system or while the data is in transit on the network.
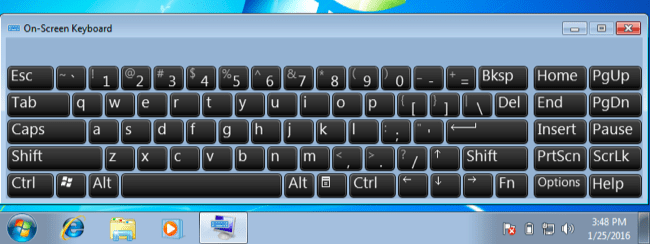
3. On-screen Keyboards
Though not a very popular method, on-screen keyboards can help in protecting against keyloggers which are logging keystrokes from the physical keyboard. However, there are keyloggers capable of taking screenshots of the screen while you enter your data. This ends up revealing your credentials to the attacker. Also, on-screen keyboards were designed as a utility for accessibility, and not to protect against cyber threats. On-screen keyboards have to be designed and implemented differently if they are to be used against keyloggers.
4. Speech Recognition
Instead of typing your credentials, you can use a speech to text conversion software and speak out your credentials. The keylogger will not log anything as no typing or mouse clicks are taking place. The weakest point in this method is the way the software sends the recognized voice to the system. The data can get intercepted if the method is not secure.
5. Network Monitors
Network Monitors (also called reverse-firewalls) alert whenever a program is attempting to make a network connection. This can give you a chance to verify the legitimacy of connection requested by the program and prevent any keyloggers form sending your typed credentials to another computer.
How to Protect Your Mac from Keyloggers using CleanMyMac X
Many people, even some Pro users, believe that Mac devices are immune to keyloggers. While it’s true that macOS is much more secure and privacy-friendly than other OSs out there, Macs too can get keyloggers. We have seen reports of malware affecting multiple Mac devices and stealing not only their passwords but also other sensitive credentials. Once a malicious program gets full disk access and accessibility features of your Mac, everything can be in trouble. In order to prevent all these, however, you will need an effective malware detection tool. And what’s most important, CleanMyMac X is checked and notarized by Apple since December 2018 as software that has no malicious components.
What is CleanMyMac X?
CleanMyMac X is a Mac cleaning utility that helps you save space, protect your device and remove unwanted stuff from your computer. It also happens to be one of the best malware detection tools in the domain. this program will not only detect the presence of keyloggers on your Mac but also remove them. As you might know, naked eyes cannot easily detect keyloggers, as they take different forms. So, at the end of the day, it is good to have a professional tool to deal with this.
There are so many other features inside CleanMyMac X, but we focus on the Malware Detection module of it. Wondering how to use CleanMyMac X Malware Detection? It’s as easy as it ever can be.
How to Use CleanMyMac X to Remove Keyloggers?
Once you have installed CleanMyMac X on your computer, you can see a bunch of options inside. You have to select the ‘Malware Removal’ section that would be analyzing your Mac for potential threats. Not only a keylogger but also other malware programs like worms, spyware, adware, miners, etc. would be detected in a few seconds.
And, as you wish, you can remove everything in a single click. It’s great if the malware scanner says that your Mac does not have any potential threats. However, it’s good to be sure by this than your own experience, you know. At the end of the day, you need just a few seconds to keep keyloggers away from your Mac. Also, make sure that you scan
your computer often using CleanMyMac X.
Compared to other
keylogger-prevention methods we talked about earlier, CleanMyMac X happens to have a straightforward process. You don’t have to worry about technical expertise or errors in this matter.
Conclusion
This article gave an overview of how to check for keyloggers, their functionalities and some precautionary measures you can employ to avoid being a victim of keyloggers. Granted, that many times, it is next to impossible to detect some of the more sophisticated keyloggers. But following the safety tips mentioned above, you should be able to protect yourself from the basic keyloggers or at least scan for keyloggers so that checking for keylogger would not be a difficult task. Also, having a fair idea and knowledge about the threat you are dealing with makes following the suggested precautionary steps more logical.





More Stories
11+ Best ThePiratebay3 Sites – Ultimate Pirate bay Alternatives
7movierulz iBomma – 11 Best Alternatives to Download & Watch latest Telugu Movies
How to Spam a Phone Number (7 best apps & services) with call, texts to Get Revenge?